using voidmap for penetration test project management
⊕ 2019-12-17
One of the hardest parts about conducting a large scale network penetration test is ensuring that everything is kept straight and that all discovered issues are tracked in a way that can be both meaningful to the tester but are also referential to the objectives of the assessment. In reality when you are dealing with networks in the scale of dozens of /8 subnets of online hosts you stop focusing on completionism and finding every single vulnerability and switch to developing a set of goals and objectives of the assessment that act as targets as well as developing the objectives as the assessment is conducted. This means that mentally keeping track of all the interconnected pieces and complex exploitation chains can quickly become unruly.
Personally I have never found a good way to collate the markdown notes I take during an engagement while also allowing me to track the complexity of the interconnections of the engagement activities. Additionally, I’ve always suffered from a context switch problem when conducting these assessments, which can really prevent me from moving quickly. These context switch triggers are:
- Switching to a non-test oriented tool or environment for managing the project objectives - think email, OneNote, mind mapping software, etc.
- Having to essentially keep different workflows for GUI and terminal use cases - for some reason the mental model for remembering workflows when working in the terminal versus with graphical programs is completely different for me.
Both of these mentally take me out of the test and end up costing me valuable time on assessments, but I’ve never found a way to square with these problems, until now.
Recently I bumped into an interesting mind mapping terminal project called voidmap that has helped organize some of these large assessments logically. I think the following example best illustrates how effective this tool can be for this use case:
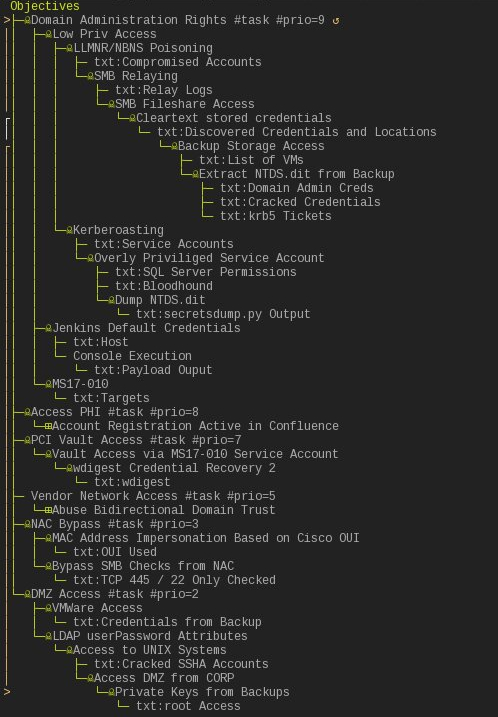
use case
voidmap is unique in the terminal project management utility space in a bunch of ways, but the following features are absolutely paramount for the large objective based network penetration test:
- Tree based - this helps organize the project while also easily allowing objectives to have multiple paths of attack that stand out visually. Collapsing is always really nice as well
- File entries - the voidmap
txt:entry allows you to store files in the voidmap database while simply using$EDITORto make changes to the entry. This is extremely helpful for keeping evidence or tool output as well as lets me keep my files in simple markdown - Terminal based - not having to switch my mental paradigm from terminal to GUI programs is really helpful but has been beaten to death, so I won’t harp on it
- Referential - entries can reference each other allowing you to reference other findings or entries with visual markings
The way I use voidmap is to define the objectives of the assessment at the very initiation of the project and then create those objectives in voidmap under a global Objectives entry even before beginning the test. After beginning testing I generally don’t need to use voidmap, I focus mostly on the normal penetration testing activities of finding my initial foothold; scanning, enumeration, etc. In the above example I start the engagement like follows, which shows 6 objectives I defined, a special voidmap #task tag, and a #prio tag which sets the voidmap task priority (in reality I don’t use these priority tags, but they help document which objectives are most import to me or the client):
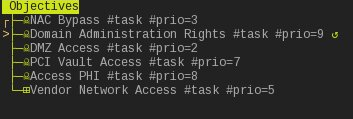
Then once I gain the foothold into the network I make a guess to where it best applies and just create it there, don’t worry they can be rearranged later. This allows me to start thinking more in my attack paths and about what the objectives are instead of focusing on artifacts in a vacuum.
voidmap additionally has support for a special txt: tag that I mentioned earlier. By simply hovering over a node with this tag and hitting Ctrl+k you get dropped into your editor and can clearly see any notes in the file.
The txt: tag lets me keep separate and embedded notes inside the map itself and clearly use the marking to tie nodes together. After I mark nodes as related you can truly start to take advantage of the ability to visually rearrange voidmap. Here is an example of the default drill-down view of the fake penetration test.
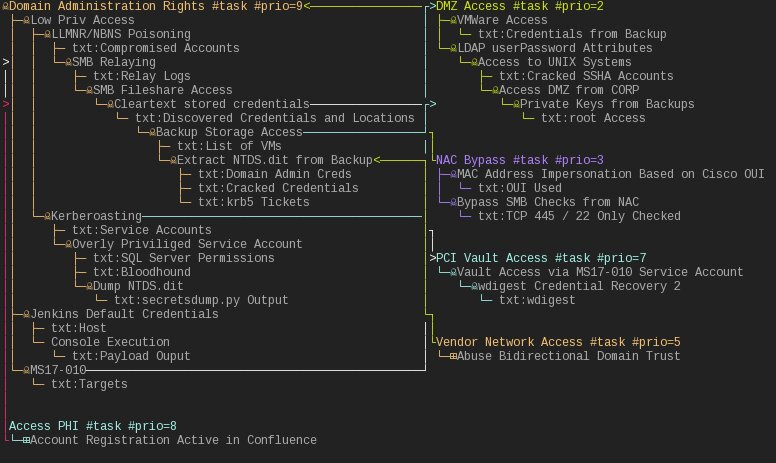
Now here is that same test broken into a different view, where I simply drilled down to view the objectives and then manually rearranged the nodes with the mouse.
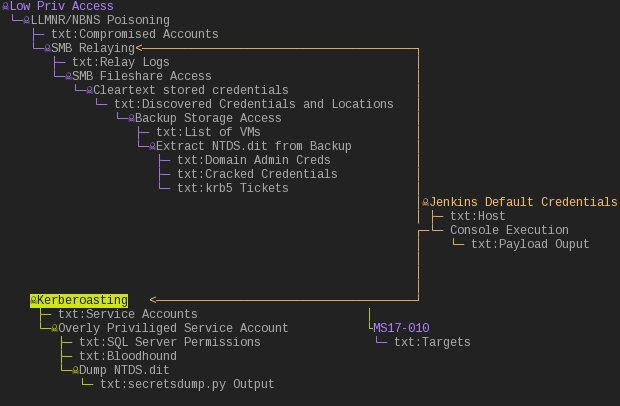
This exact setup has been so effective for me that I’ve used it to show off to clients and co-workers alike some progress that has been made during an engagement.
conclusion
voidmap is a unique tool for keeping a large assessment in your head while also allowing for showing off of your progress that for the first time makes me feel in control of these engagements. One of the most important things to keep in mind is that graph theory lets us move away from traditional non-interconnected findings and security thinking, and instead lets us see hidden interconnections and attack paths. voidmap helps make that a mental reality.
I’ve been teaching it to many other pentest friends over the last few months and I hope it gets some more love. Go check out voidmap.